This guide provides step-by-step instructions on how to analyse a malware sample on ANY.RUN. By following these steps, users can navigate the platform, search for existing malware samples, view connections and network traffic, collect IOCs, and gather more information about the threat.
Navigate to ANY.RUN
Go to ANY.RUN.
Public Tasks
Click “Public tasks” to view the public directory and submissions from the community.
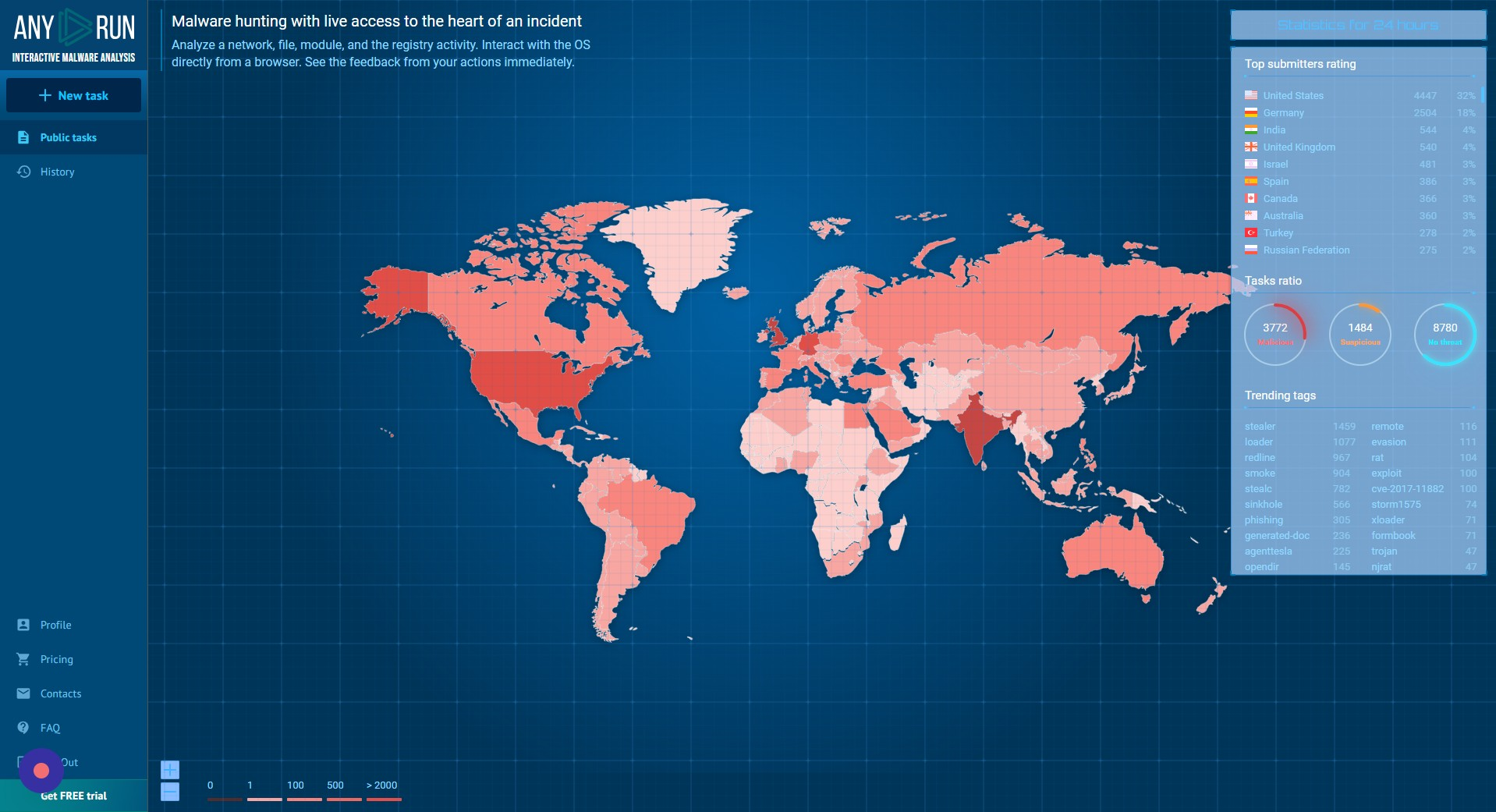
Filter by Tag, Hash, or IOCs
Click here to filter by tag, hash, or other IOCs. This method allows us to quickly analyse existing malware samples instead of setting up our own sandbox.
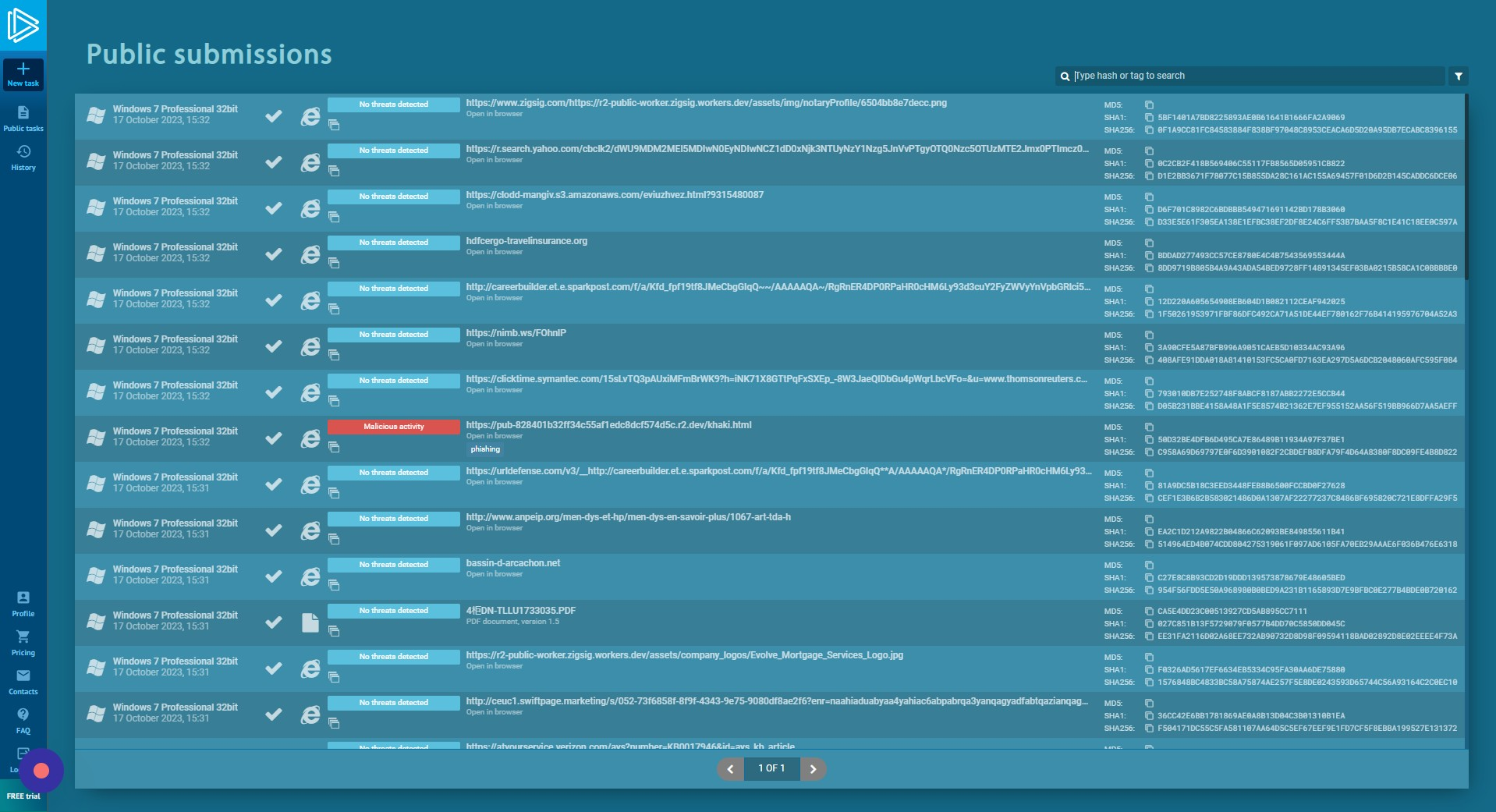
Search for Malware Samples
Search for any malware sample listed in the public directory. In this case, we are using the ransomware “lockbit”.
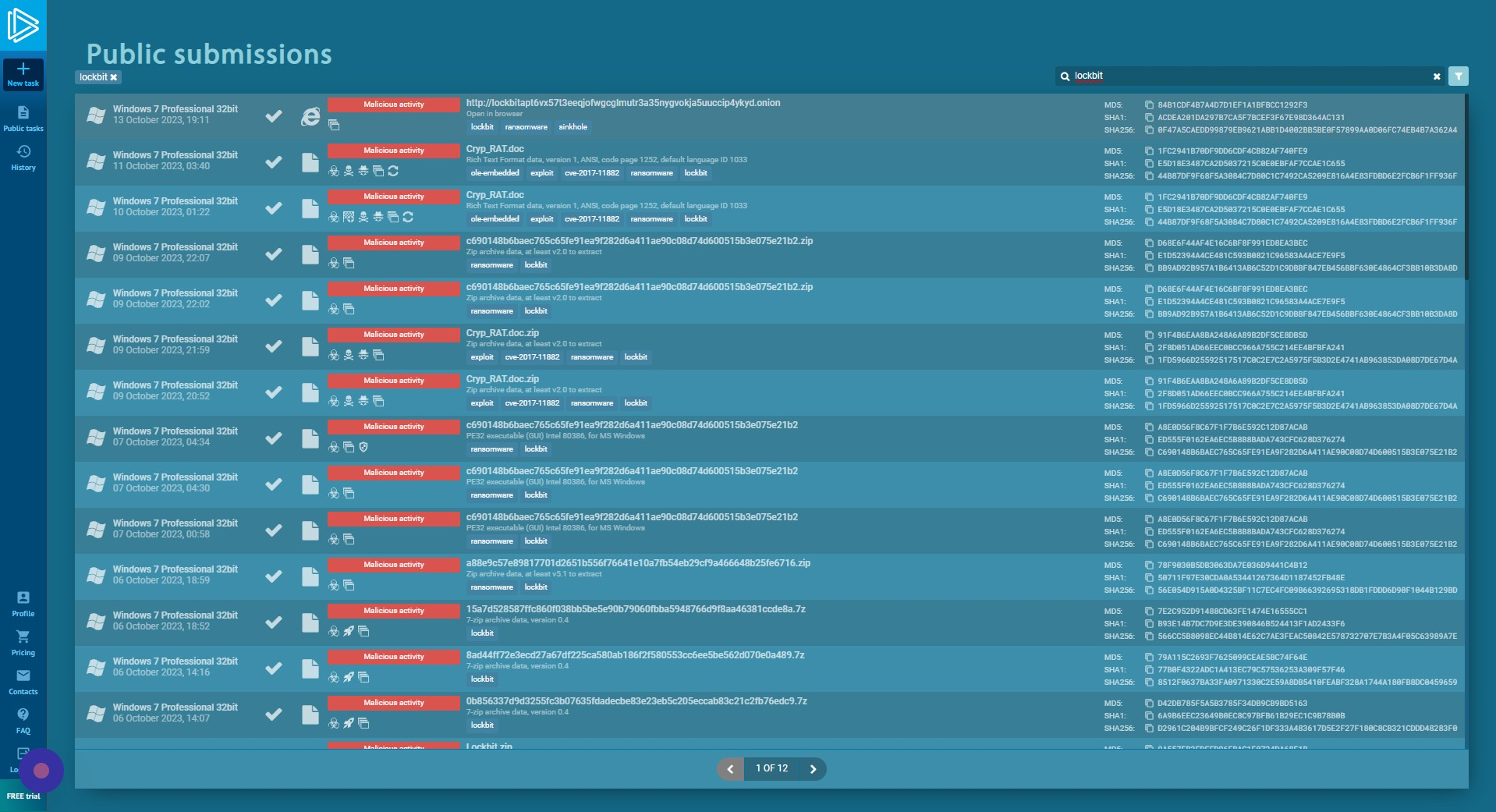
Select a Sample
Click on the sample references as malicious and matching the tag “lockbit”. In this case, we are selecting the first sample in the list, referencing a .onion link.
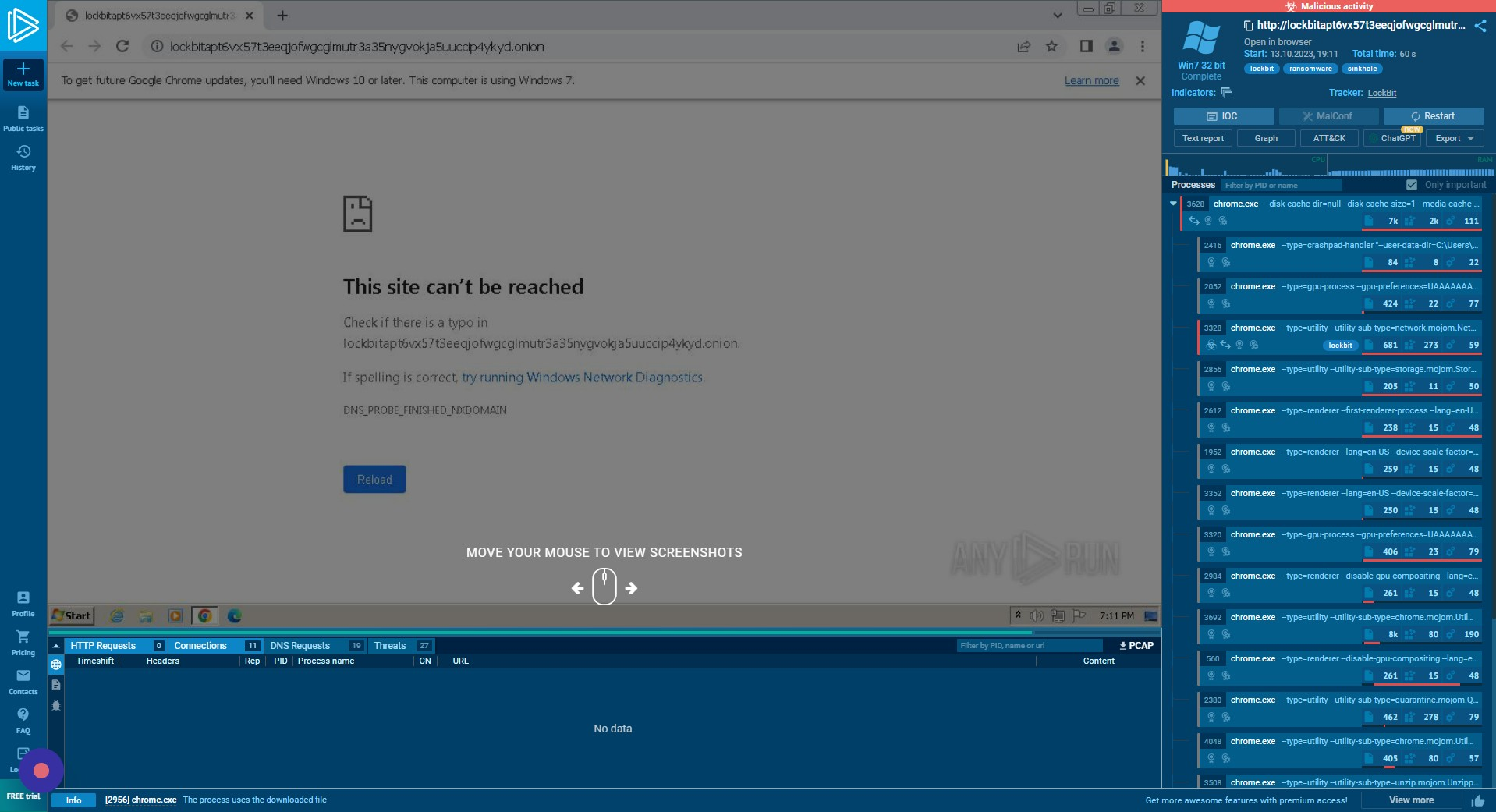
Connections Tab
The “Connections” tab allows you to view connections to and from this host during the sample analysis. This provides a holistic view of processes, ports, and traffic.
DNS Requests Tab
The “DNS Requests” tab provides a holistic view of connections to domains and their resolved IP(s).
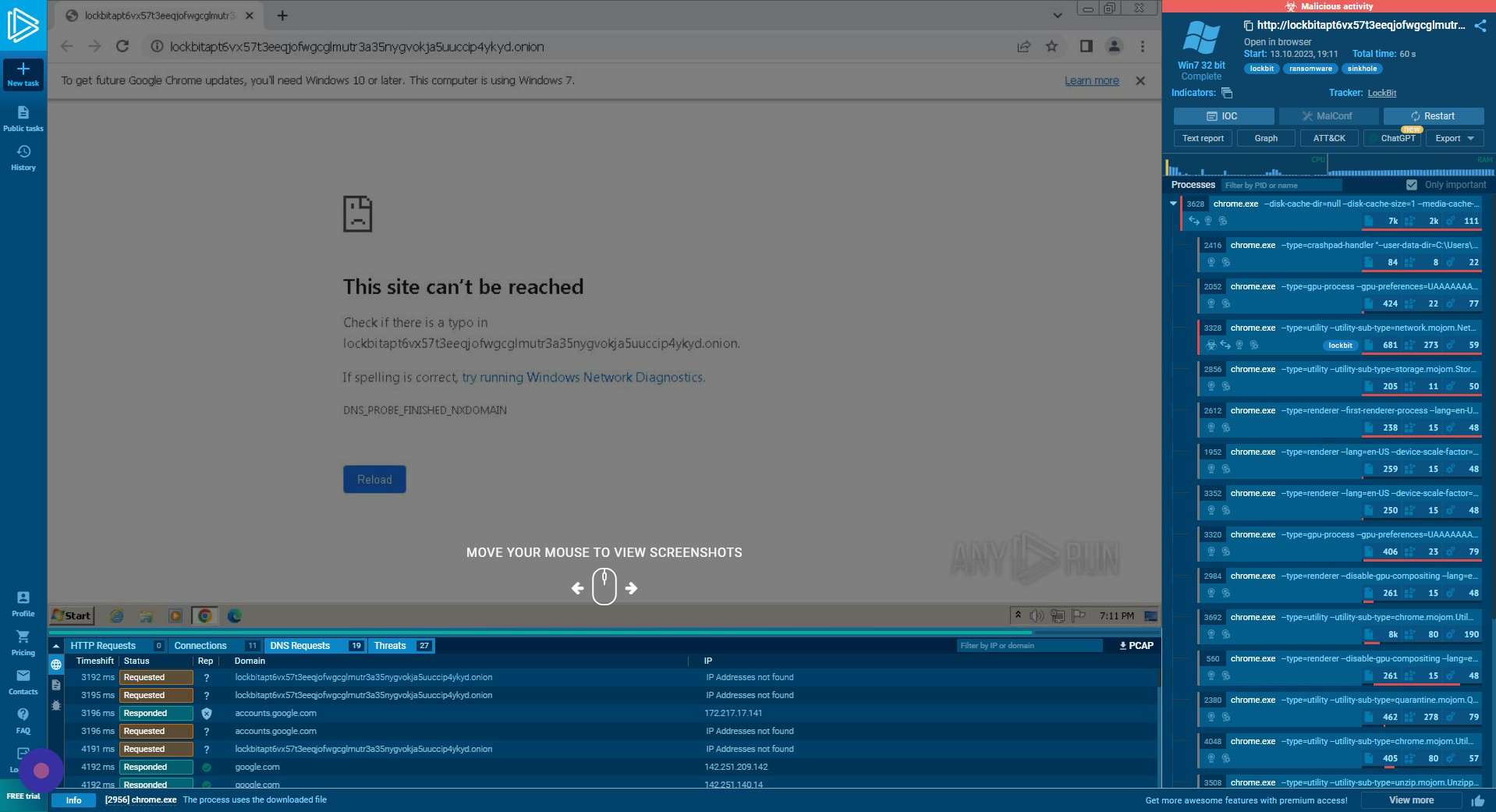
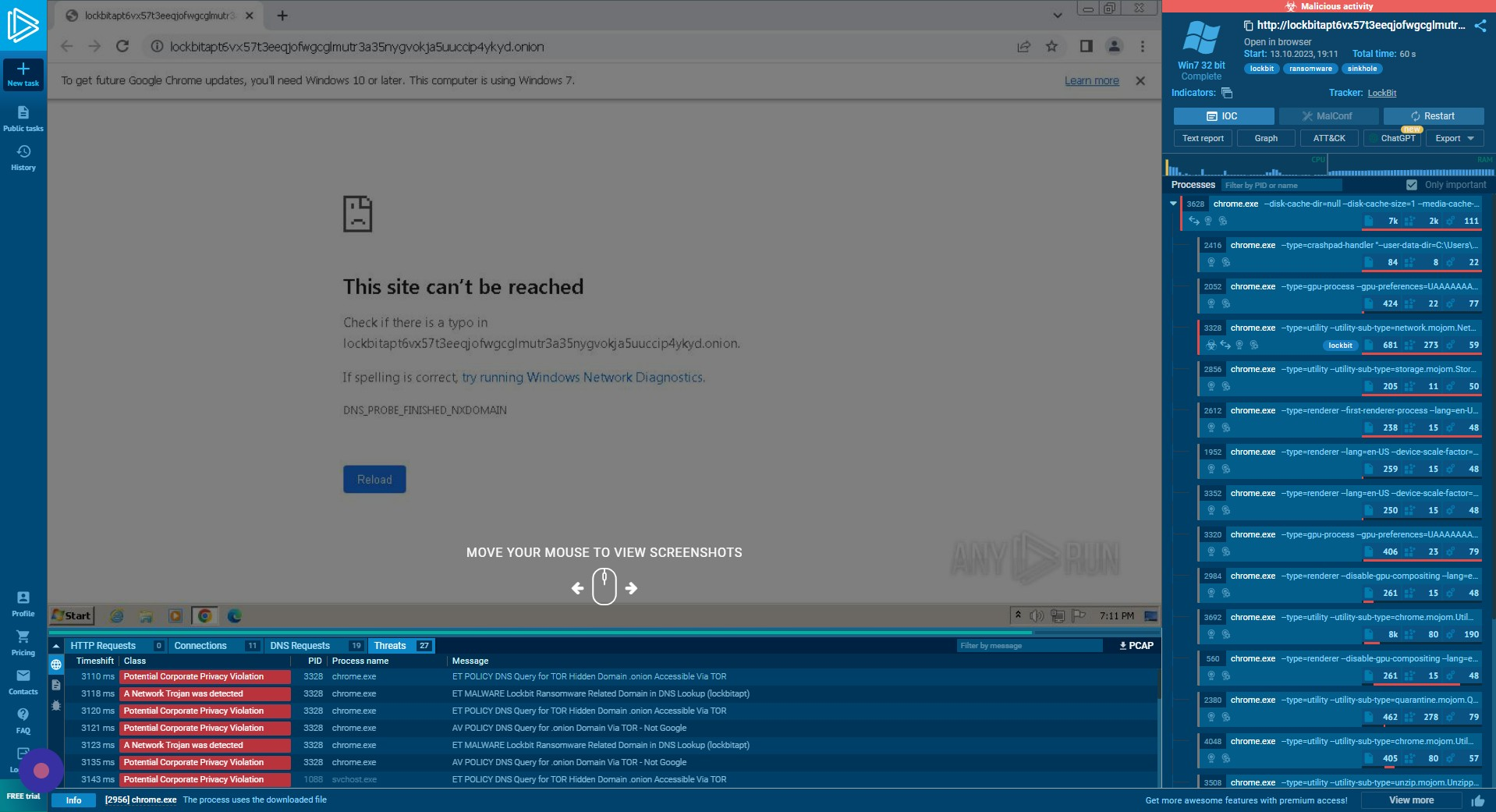
Threats Tab
The “Threats” tab provides a view of the specific processes and known threats associated with these.
IOC Tab
The “IOC” tab provides a summary of the detected Indicators of Compromise.
Processes Tab
You can drill down into individual processes in order of execution using the “Processes” tab on the right-hand side.
Alternatively, a graphical representation of the list of processes can be viewed using the “Graph” button.
Process Details
More details can be viewed by clicking on the process.
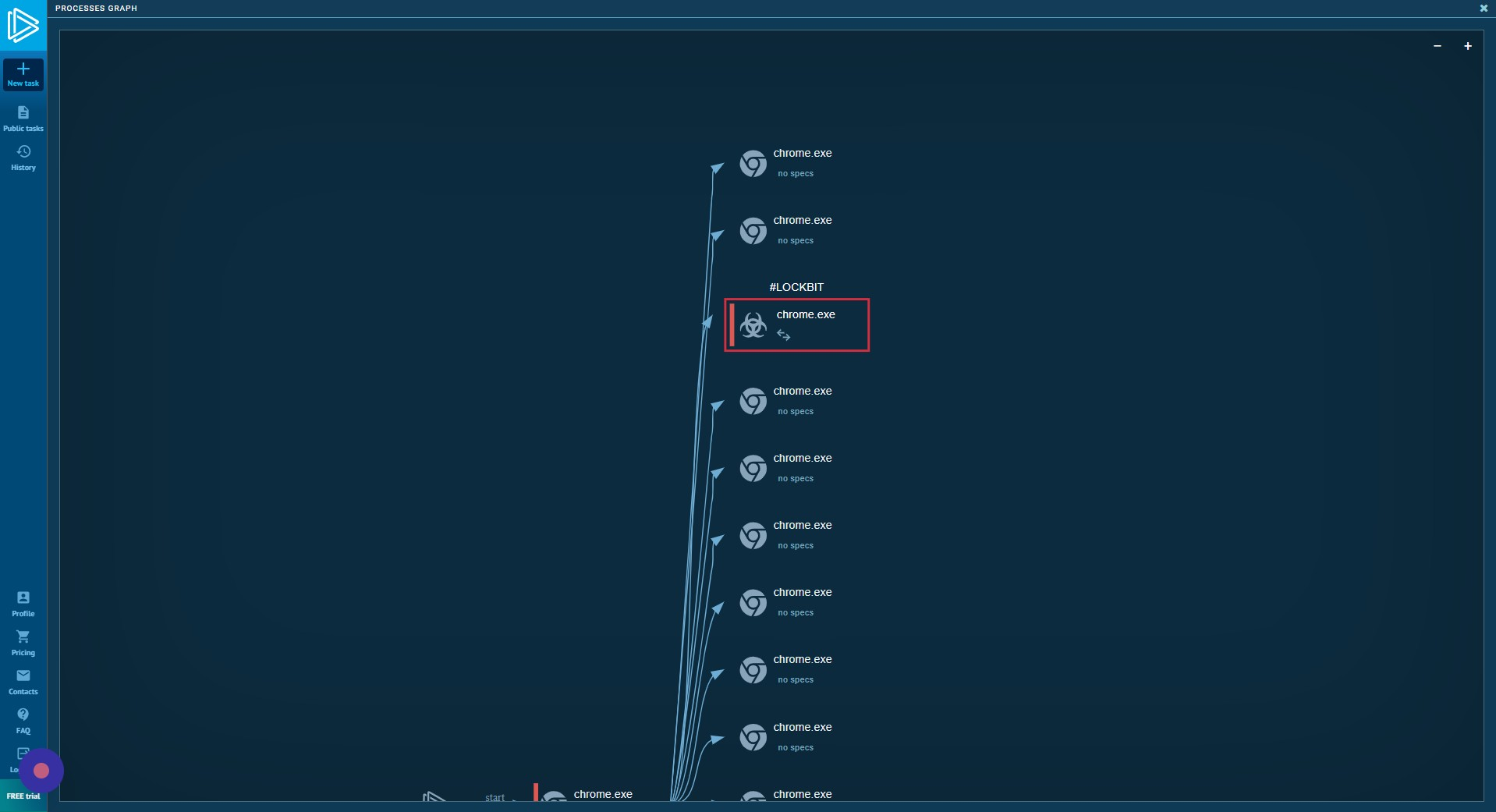
Child Processes
Reverting back to the list view, you can also view child processes spawned in the list.
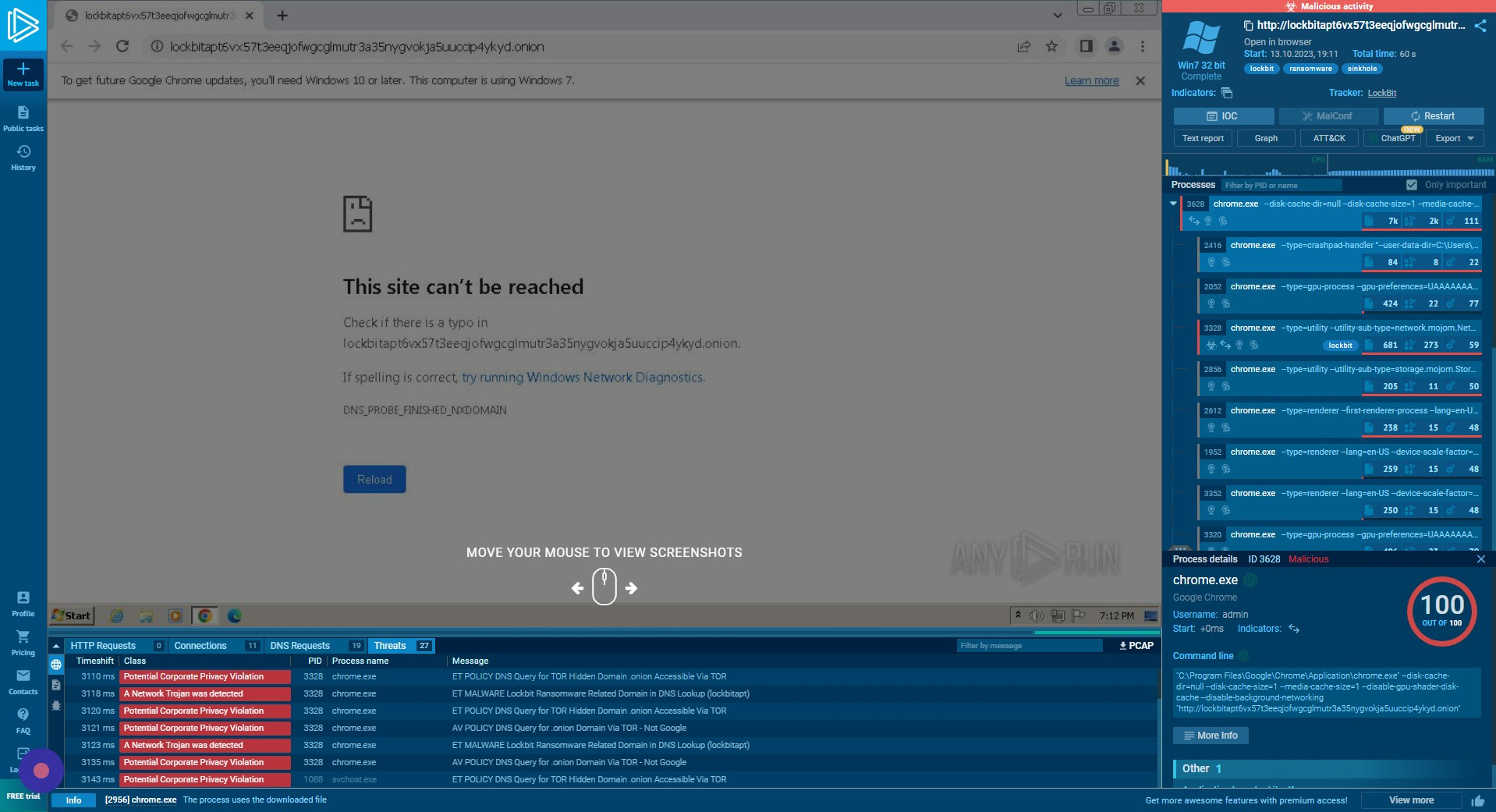
Specific Process Example
The third process spawned in this sample is chrome.exe with the tag “lockbit” indicating that this process may be the execution stage of the attack.
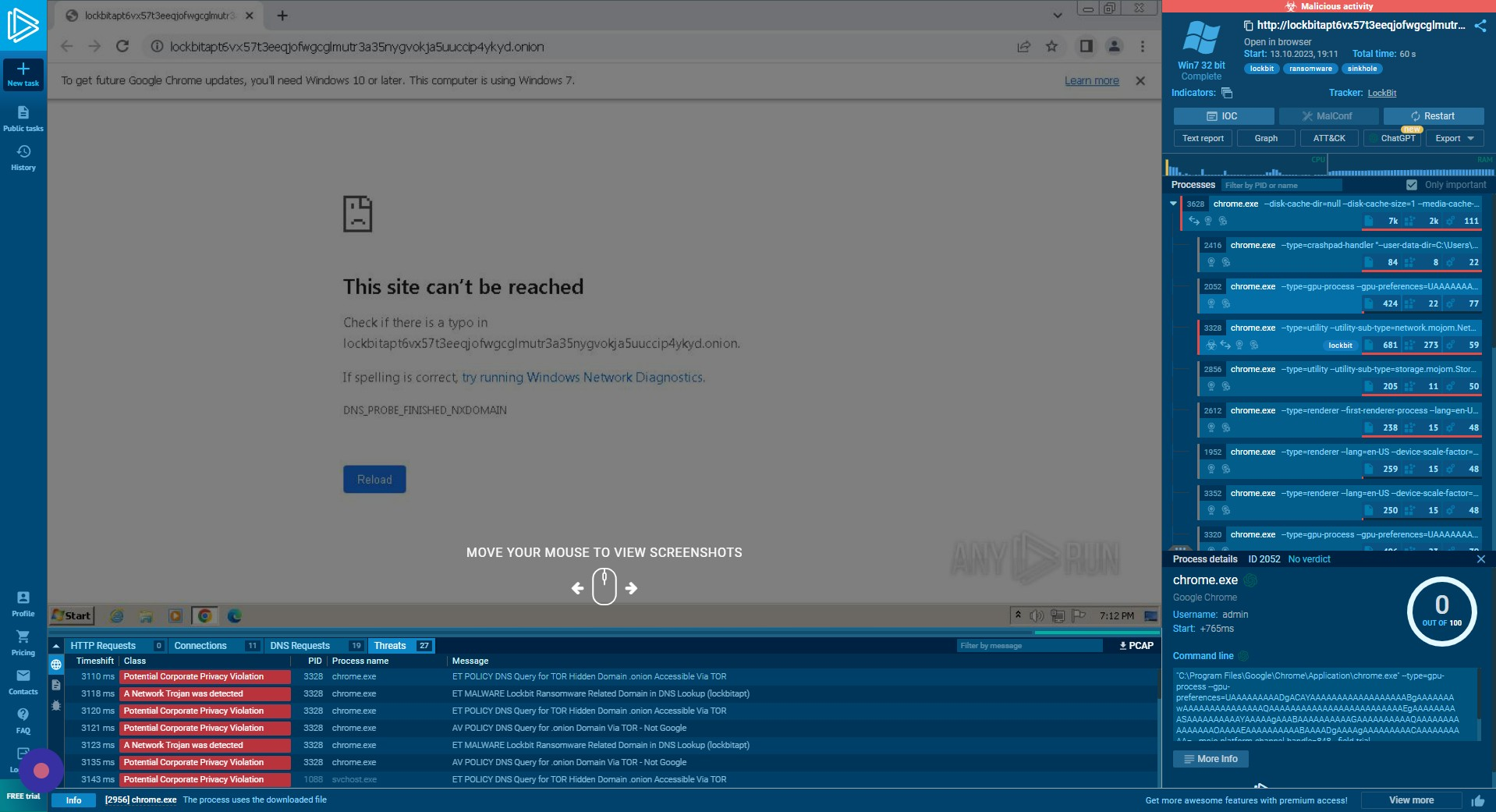
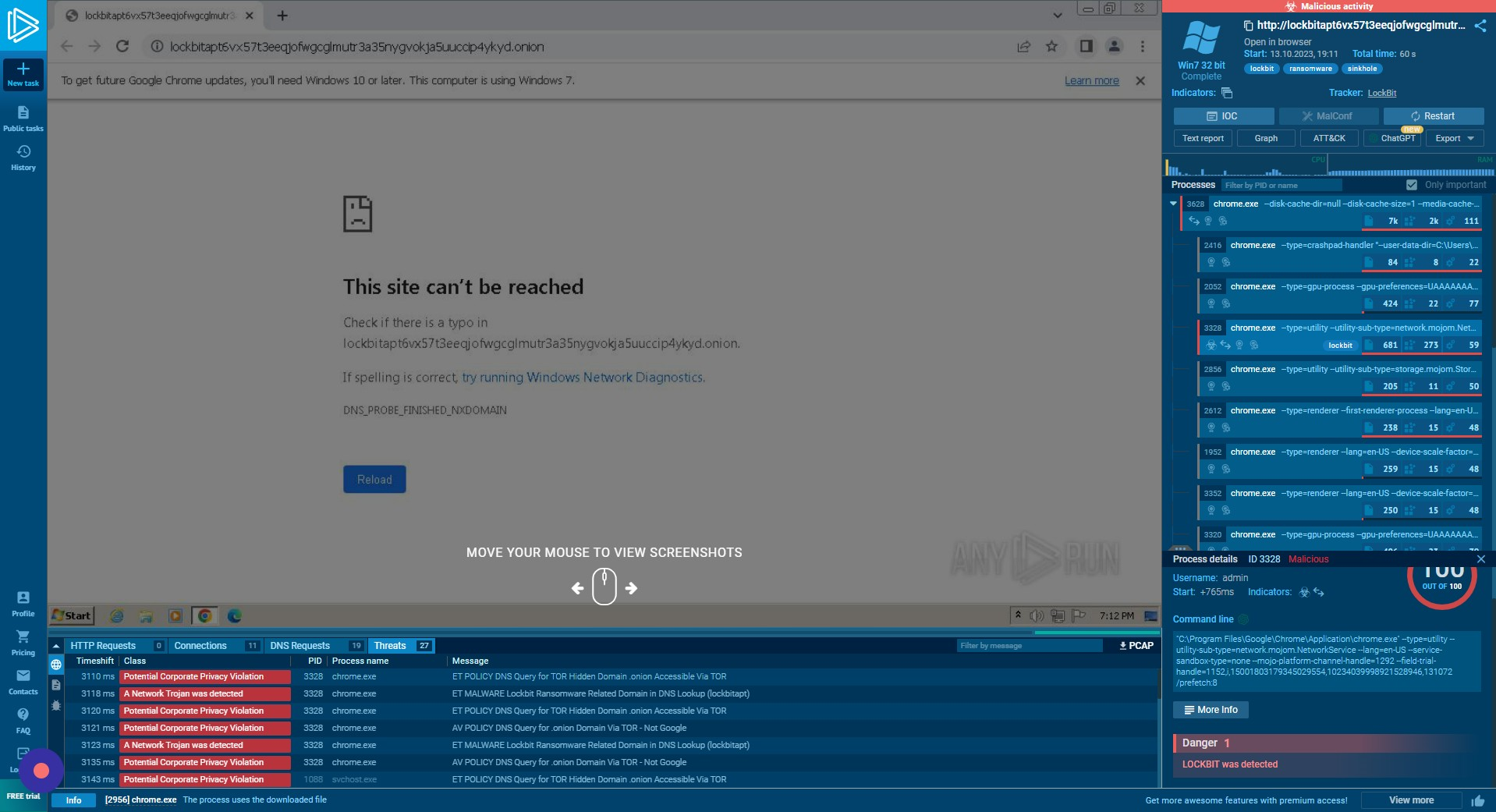
More Info
If we click “More Info”, we can view the command line arguments performed by the system to launch this process and more details on the process executed.
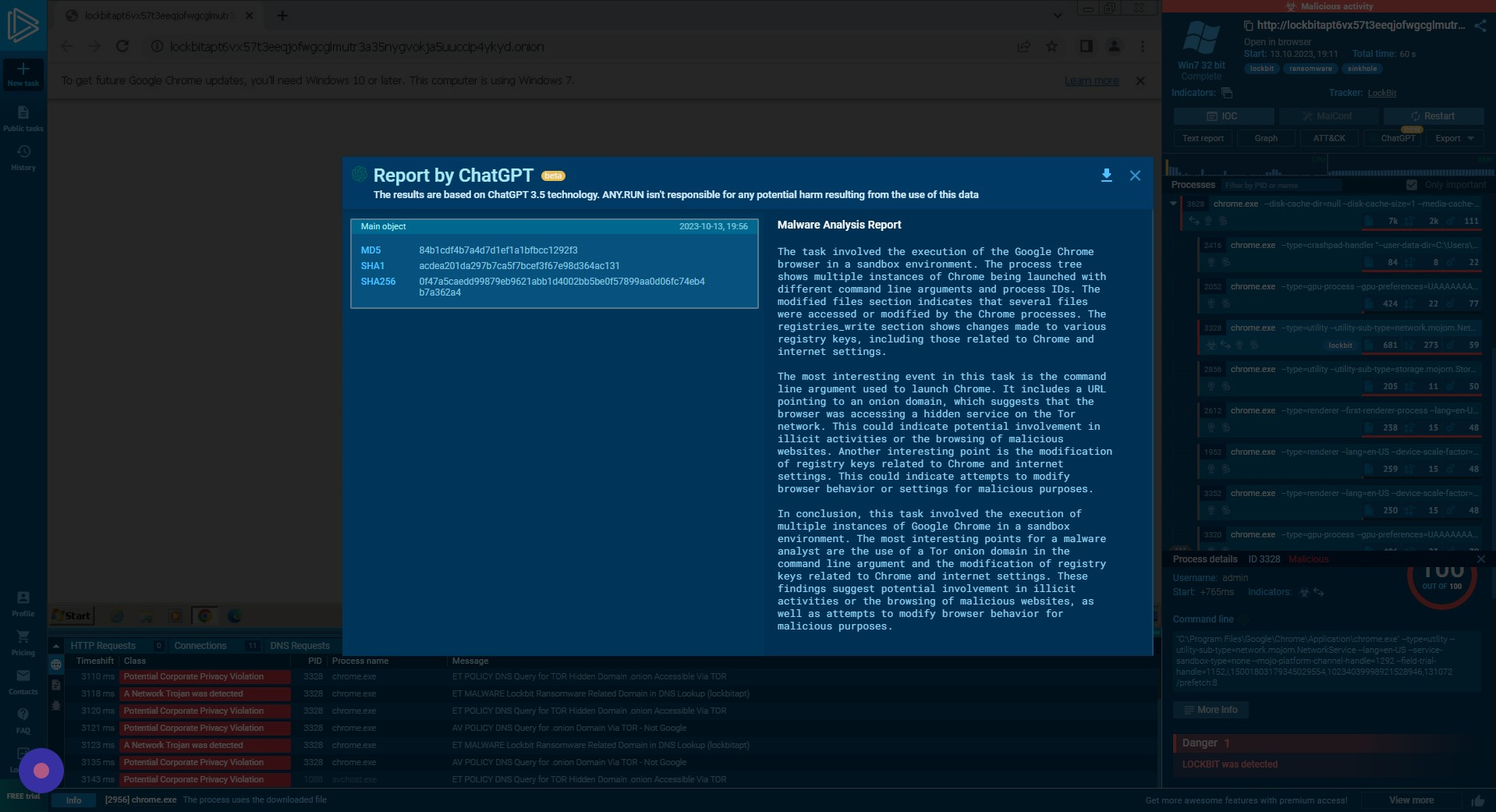
ChatGPT3.5 Integration
Using the ChatGPT3.5 integration, we can view a summary of what is going on. While this may not be 100% accurate, it can help provide an initial understanding of the attack story.
Reporting and Exports
JSON Export
Optionally, a JSON export of this ChatGPT summary report can be downloaded.
Detailed Text Report
Finally, a detailed text report can be downloaded from the browser by clicking on the text report button.
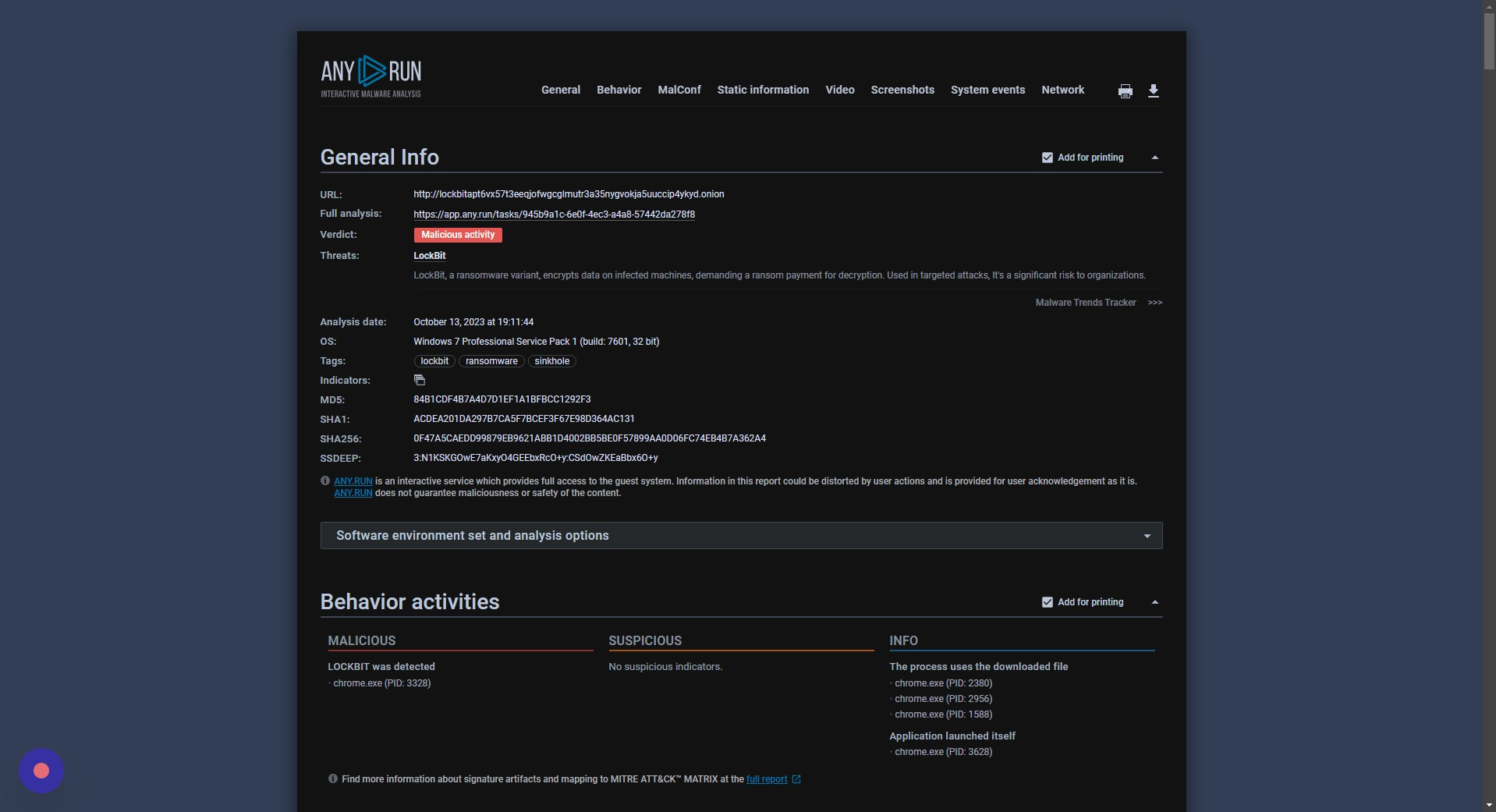
Full Analysis
The full analysis for the sample showed in this tutorial was previously available on ANY.RUN, but the link is no longer active as this analysis was performed some time ago.
Note: ANY.RUN’s sandbox is an excellent resource for malware analysts, providing a quick way to understand malware behavior without having to set up your own analysis environment. However, remember that some samples might be removed or become unavailable over time.